AWS Sessions Manager allows us to remotely connect to a virtual machine without the use of an SSH key. This is allows for much better security posture because you do not have to worry about stolen or lost SSH keys and its easily to grant access to machines. You can remotely connect from any machine because its all done through the AWS Console and you have an audit history of who logged in.
In order to use Sessions Manager we need two things:
- The SSM Agent
- An AWS role attached to the VM with a policy to use Sessions Manager
Installing the Agent
Since Forem uses Fedora OS it does not have the agent preinstalled like Amazon Linux 2, but it is not difficult to install.
Login via SSH
ssh core@54.164.107.192 -i ~/.ssh/id_rsa.pub
Installing the SSM agent
sudo rpm-ostree install https://s3.us-east-1.amazonaws.com/amazon-ssm-us-east-1/latest/linux_amd64/amazon-ssm-agent.rpm
The agent says to reboot your machine, so you'll need to do this wait a little while and then SSH back in.
sudo systemctl reboot
ssh core@54.164.107.192 -i ~/.ssh/id_rsa.pub
Observe the SSM Agent layer being managed by RPM-OSTree
rpm-ostree status
Make sure the SSM agent is running
So running the service status command:
sudo systemctl status amazon-ssm-agent
shows that is currently not running eg. inactive (dead)
○ amazon-ssm-agent.service - amazon-ssm-agent
Loaded: loaded (/etc/systemd/system/amazon-ssm-agent.service; disabled; vendor preset: disabled)
Active: inactive (dead)
So lets start it, and enable it (make sure it always starts when the system is rebooted)
sudo systemctl start amazon-ssm-agent
sudo systemctl enable amazon-ssm-agent
and lets reboot our system to make sure that enable is working
sudo systemctl reboot
##Wait a little while for the system to reboot
ssh core@54.164.107.192 -i ~/.ssh/id_rsa.pub
Running status again you should now see that its running:
core@www (www.thedev.cloud) ~]$ sudo systemctl status amazon-ssm-agent
● amazon-ssm-agent.service - amazon-ssm-agent
Loaded: loaded (/etc/systemd/system/amazon-ssm-agent.service; enabled; vendor preset: disabled)
Active: active (running) since Thu 2021-07-22 16:59:31 UTC; 2min 48s ago
Main PID: 750 (amazon-ssm-agen)
Tasks: 16 (limit: 2239)
Memory: 51.8M
CPU: 172ms
CGroup: /system.slice/amazon-ssm-agent.service
├─ 750 /usr/bin/amazon-ssm-agent
└─1026 /usr/bin/ssm-agent-worker
Jul 22 16:59:32 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO no_proxy:
Jul 22 16:59:32 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO Agent will take identity from EC2
Jul 22 16:59:32 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO [amazon-ssm-agent] using named pipe channel for IPC
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO [amazon-ssm-agent] using named pipe channel for IPC
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO [amazon-ssm-agent] using named pipe channel for IPC
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO [amazon-ssm-agent] amazon-ssm-agent - v3.0.1390.0
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:32 INFO [amazon-ssm-agent] OS: linux, Arch: amd64
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:33 INFO [amazon-ssm-agent] [LongRunningWorkerContainer] [WorkerProvider] Worker ssm-agent-worker is not>
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:33 INFO [amazon-ssm-agent] [LongRunningWorkerContainer] [WorkerProvider] Worker ssm-agent-worker (pid:1>
Jul 22 16:59:33 www.thedev.cloud amazon-ssm-agent[750]: 2021-07-22 16:59:33 INFO [amazon-ssm-agent] [LongRunningWorkerContainer] Monitor long running worker health every 60 sec>
lines 1-21/21 (END)
Giving the EC2 instance permission
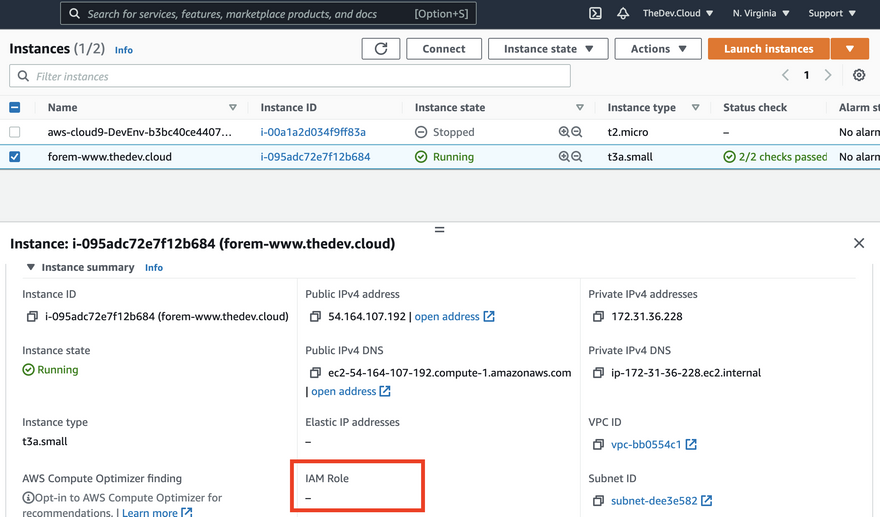
Observe no role attached on EC2 instance
Using the navigation in the top, navigate to EC2 and in the left hand side click on Instances.
You will have an EC2 instance running forem, and I want you to observe that there is currently no attached role.
Create a new IAM Role
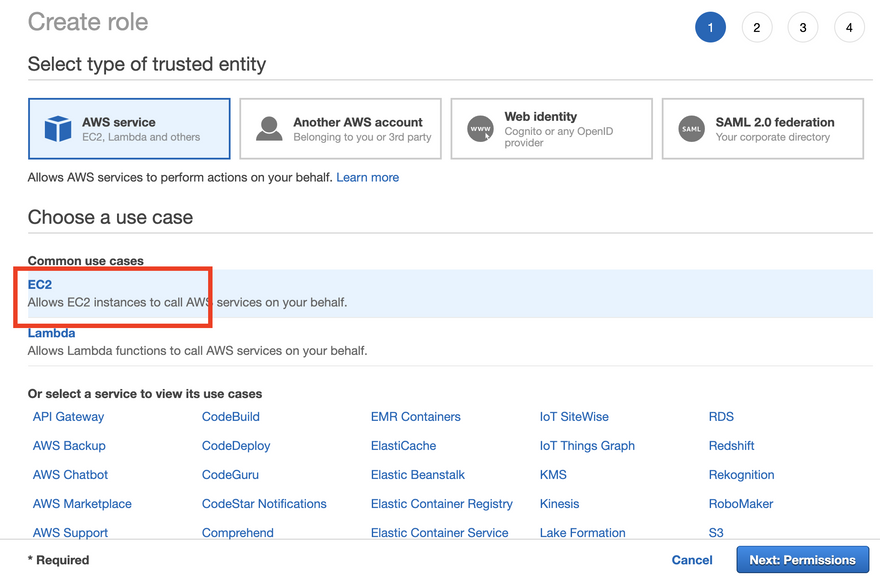
Using the navigation in the top, navigate to IAM and in the left hand side click on Roles and Create a new role.
We want to choose EC2 because this is who we are giving permission to:
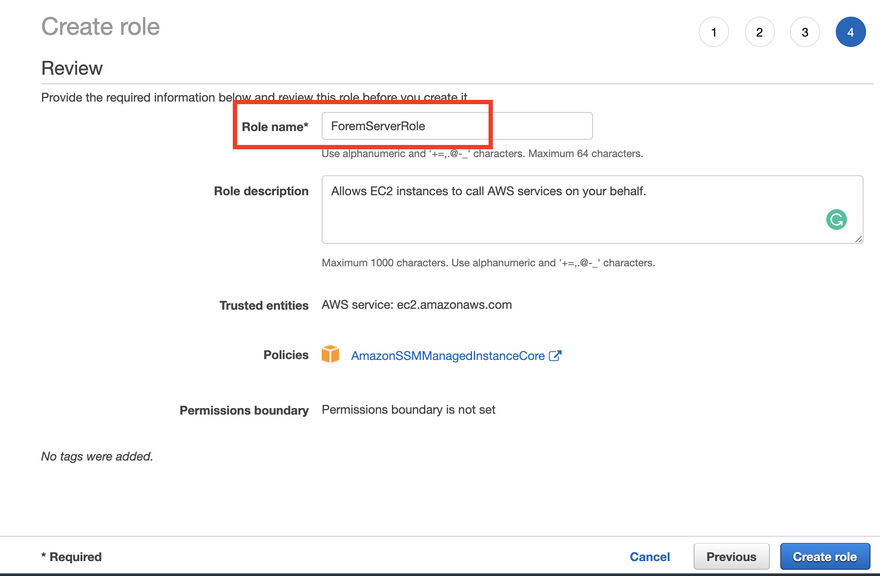
For permissions we want AmazonSSMManagedInstanceCore so type in Core and select it, proceed to tags and then proceed to review.
Name your Role, I recommend something like ForemServer and create the role
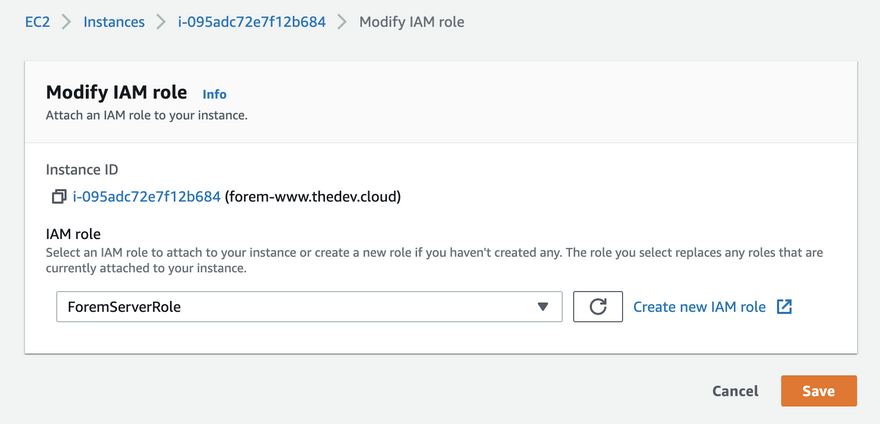
Attach IAM Role to EC2 server
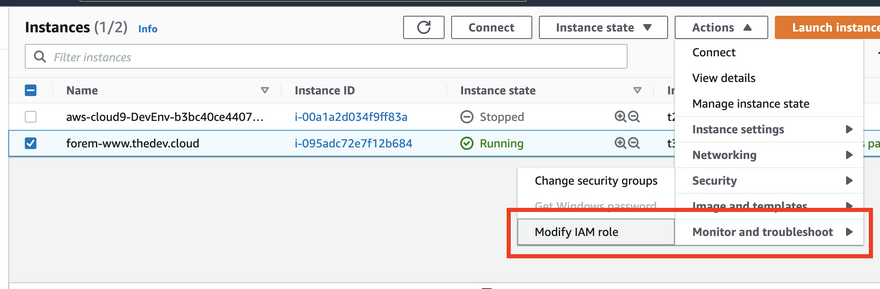
Now that we have the role lets go back to our EC2 instance.
Dropping down Actions to Security and clicking Modify IAM role
We can go ahead and attach our role
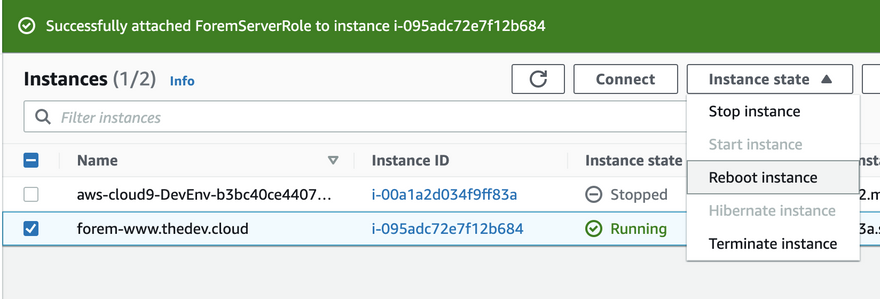
Because we did not have any role previously attached, our instance never had AWS credentials on the machine, so the first time you attach a role, in order for it take proper effect you need to reboot your EC2 instance. If we were to modify the role or change the role to a different role it will not require a reboot in the future.
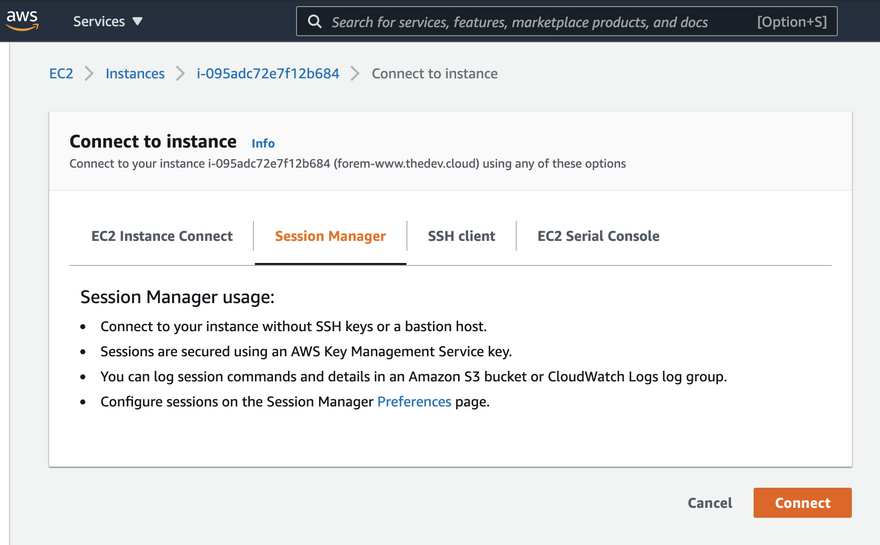
Connecting via Sessions Manager
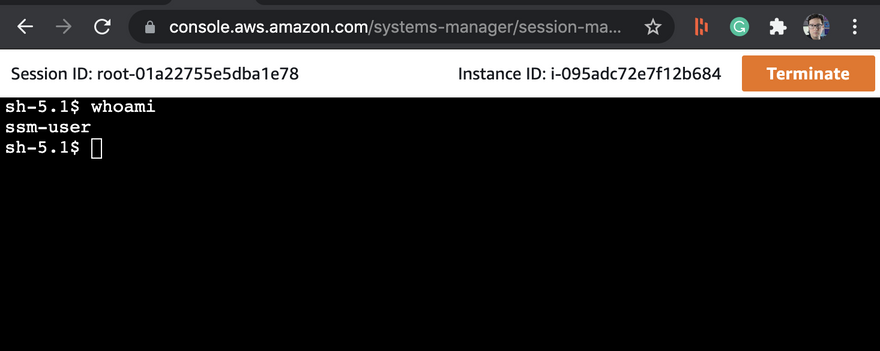
We will connect via Sessions Manager
When you connect to an instance you will be logged in as the ssm-user
Typing whoami will show you what user you are.
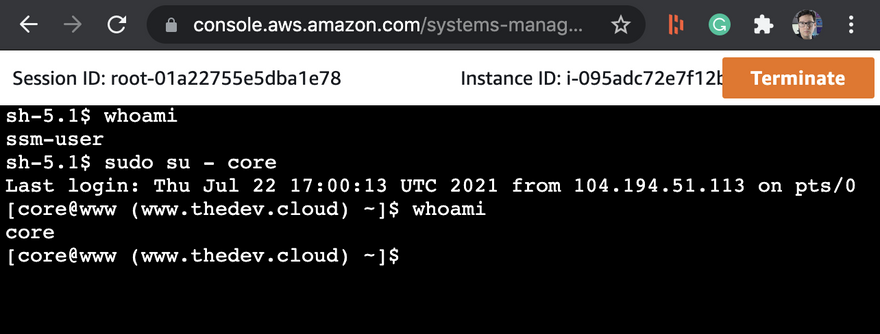
We need to be the core user so we can use sudo su to change users
sudo su - core
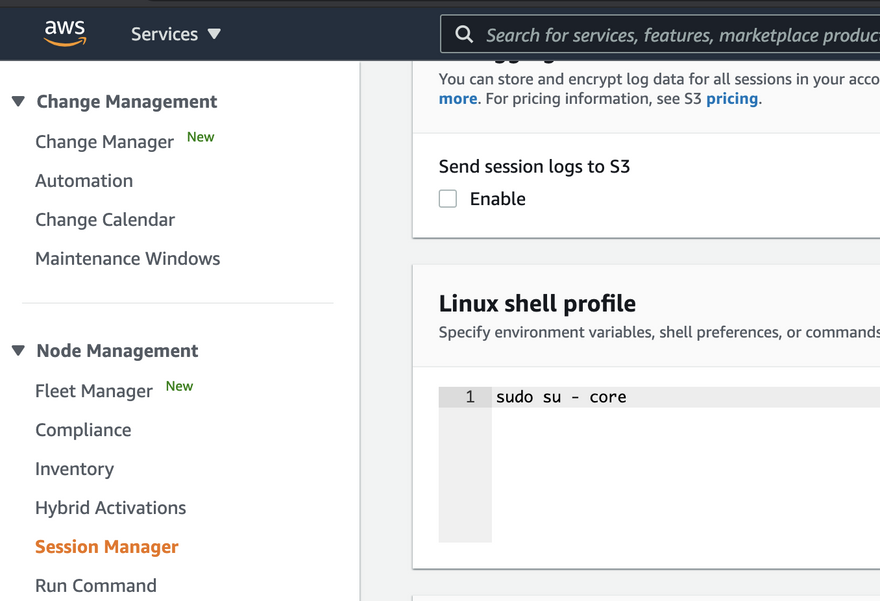
If you don't want to have to type sudo su - core everytime you use Sessions Manager you can navigation to Systems Manager via the navigation, go to Sessions Manager go to Preferences and then add a default linux script
Consider that this will happen for any VM you use Sessions Manager for so if you have a mix of VMs you might not what to set the default setting.
Conclusion
We have improved our Security Posture, never have to worry about lost or stolen keys and can access our server any browser!






Top comments (0)